4.2.4.2 System of reliable linking/resolution services in order to find identified objects
The repository shall have a system of reliable linking/resolution services in order to find the uniquely identified object, regardless of its physical location.
This is necessary in order that actions relating to AIPs can be traced over time, over system changes, and over storage changes.
Documentation describing naming convention and physical evidence of its application (e.g., logs).
A repository needs to ensure that there is in place an accepted, standard naming convention that identifies its materials uniquely and persistently for use both in and outside the repository. The ‘visibility’ requirement here means ‘visible’ to repository managers and auditors. It does not imply that these unique identifiers need to be visible to end users or that they serve as the primary means of access to digital objects. Ideally, the unique ID lives as long as the AIP; if it does not, there must be traceability. Subsection 4.2.1 requires that the components of an AIP be suitably bound and identified for long-term management, but places no restrictions on how AIPs are identified with files. Thus, in the general case, an AIP may be distributed over many files, or a single file may contain more than one AIP. Therefore identifiers and filenames may not necessarily correspond to each other. Documentation must represent these relationships.
See section 4.2.4 for a description of how semantic identifiers are constructed to be unique and persistent. Depositors can view and search using semantic identifiers in the GUI, CLI, and API. All files contain metadata to associate them with a parent object. This information is redundant in the APTrust database and stored in the object storage headers; a PREMIS event documents the identifier assignment. Since identifiers are immutable, they will always be unique and identify the same content; this has been demonstrated through two migrations of the APTrust repository.
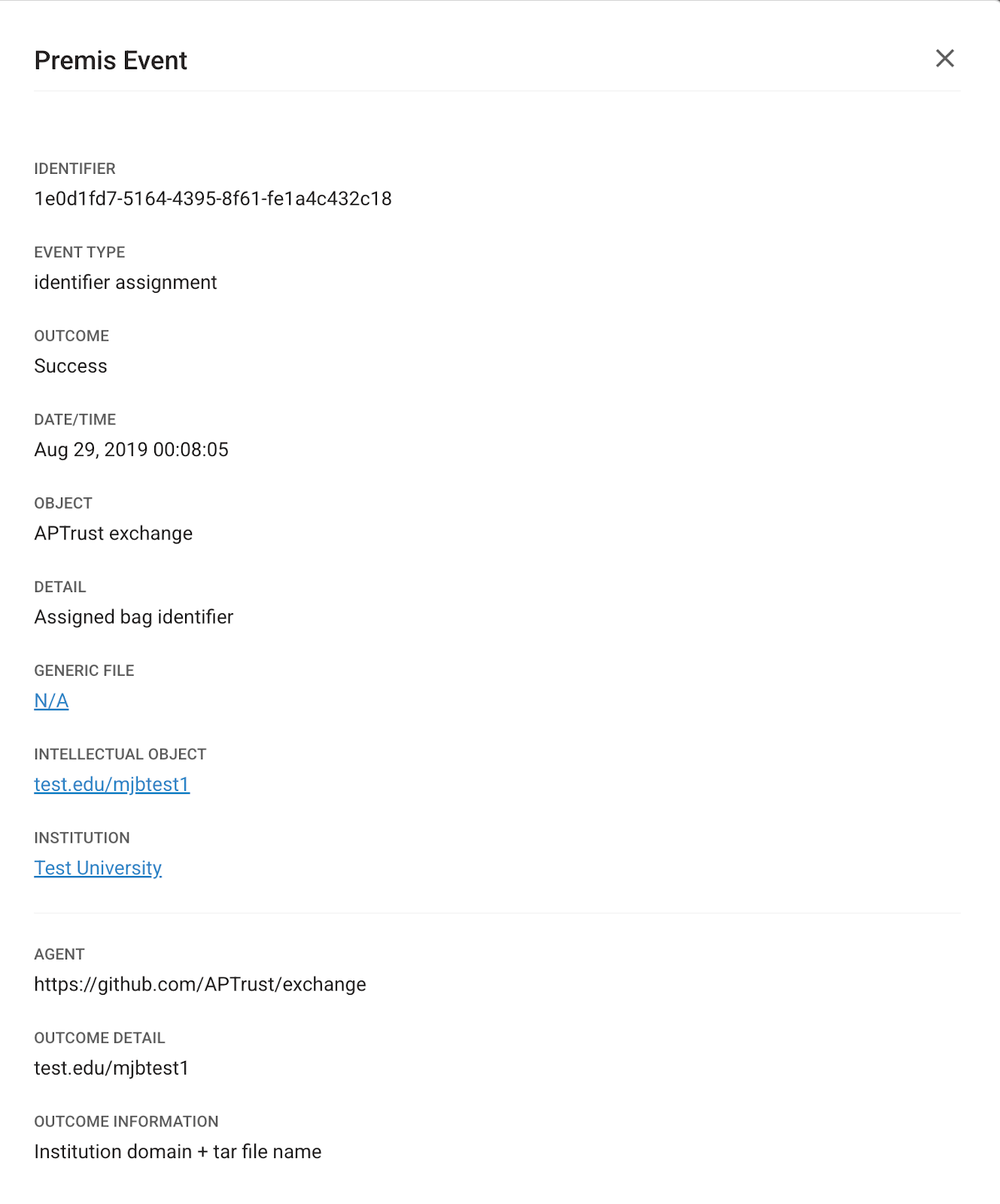
Figure 1. A PREMIS event record showing the semantic identifier (Outcome Detail) being assigned to an intellectual object.